Good cyber security is the key to reducing the risk of a cyber attack in your organisations, and its main aim is to protect our devices, the services we use them to access, and the important information stored on them.
The prospect of a cyber attack may seem scary, but we’ve put together some easy steps you can take to mitigate the risk and protect the most vital parts of your business.
1. Carry Out a Cyber Security Risk Assessment
 To figure out what measures you need to take to protect your business, you should first conduct a cyber security risk assessment. This should cover all assets that could potentially be affected by a cyber attack, and what risks could affect each asset.
To figure out what measures you need to take to protect your business, you should first conduct a cyber security risk assessment. This should cover all assets that could potentially be affected by a cyber attack, and what risks could affect each asset.
2. Use Secure Passwords
You should use strong and different passwords for every account. A good way to create more secure passwords is to combine three random words to create a long password that is hard to guess. Avoid creating passwords linked to personal information, such as birthdays, pet names, favourite sports teams etc.
3. Turn on 2-Step Verification
 2-step verification asks you to prove your identity when you try to log in, so even if someone has your passwords, they won’t be able to access your account. This often comes in the form of a code sent to your phone, but may also include confirmation via a secondary email address.
2-step verification asks you to prove your identity when you try to log in, so even if someone has your passwords, they won’t be able to access your account. This often comes in the form of a code sent to your phone, but may also include confirmation via a secondary email address.
4. Make Regular Backups
Some cyber attacks involve malware, which can erase or corrupt data, or ransomware, which holds your files ‘hostage’ until a payment is made to the attacker. In the case that this happens, backups can help you to recover with minimal damage. You should regularly backup your most important documents, and know how to restore them if needed. Backups should be kept separate from your main network, either offline in a different location, or on a cloud-based service.
5. Take Preventative Action Against Malware
There are steps you can take to prevent malware from being delivered and spreading through devices. These include:
- Mail filtering – this can be used to block malicious emails and remove dangerous attachments
- Internet security gateways – these inspect content for known malware
- Safe browsing lists in web browsers – these can prevent access to sites known to be hosting malicious content
- Intercepting proxies – which block known malicious websites
These services tend to be applied at a network level rather than on individual user devices.
 6. Keep Your Devices Up To Date
6. Keep Your Devices Up To Date
Ensure your devices have the latest software updates to make sure that they have the latest security measures, reducing the risk of cyber threats.
7. Prepare for an incident
You know what they say – if you fail to plan, you plan to fail!
In case you are faced with a cyber incident, make sure you’ve taken the following steps to prepare:
- Identify your critical electronic information – this may include key systems, resources, contact details, calendars and essential documents
- Maintain your backups – test that your backup if working regularly to ensure you can restore information from it if needed
- List your key partners – Have contact details to hand for important people, such as suppliers, customers and IT support so that you can access them even if your systems are down
- Make an incident plan – Know what steps you have to take in came of an emergency, and keep the plans safe in case you do not have access to electronic equipment
8. Protect Your Mobile Devices
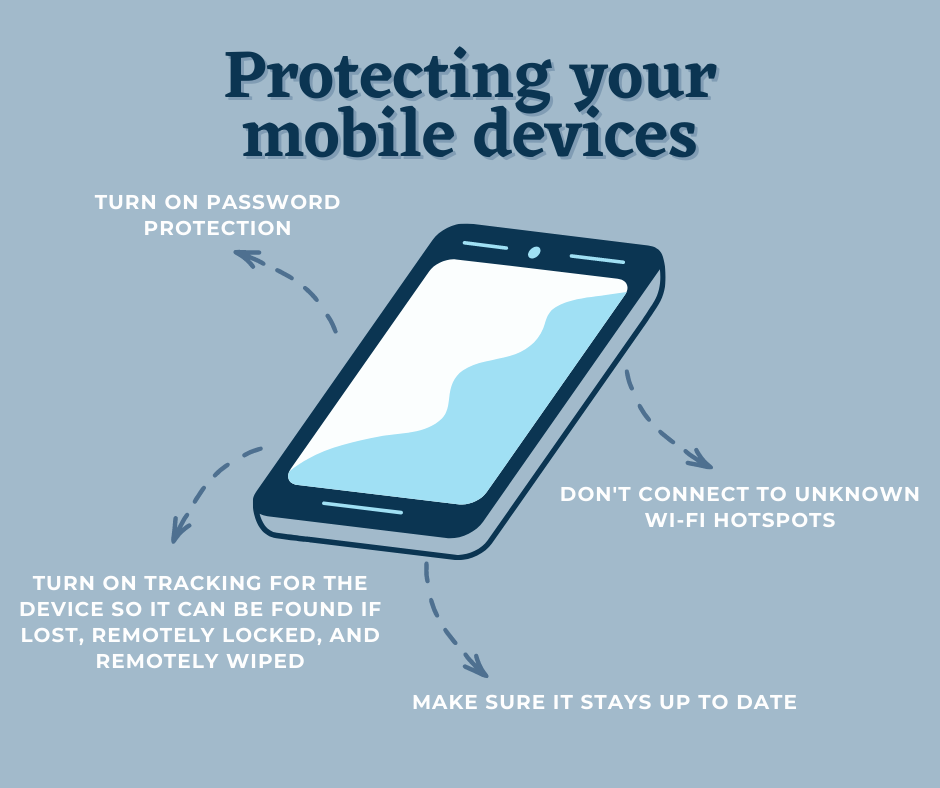 Mobile devices are an integral part of many businesses, and require further protection due to their portable nature – here are some steps to keeping your devices safe:
Mobile devices are an integral part of many businesses, and require further protection due to their portable nature – here are some steps to keeping your devices safe:
- Turn on password protection
- Turn on tracking for the device so it can be found if lost, remotely locked, and remotely wiped
- Make sure it stays up to date
- Don’t connect to unknown Wi-Fi hotspots
9. Take a Multi-Layered Approach to Phishing Protection
The National Cyber Security Centre advises that four layers of mitigations are required to defend your organisation from phishing attacks. They recommend the following actions:
- Make it difficult for attackers to reach your users – block and filter phishing emails, introduce anti-spoofing controls, etc.
- Help users identify and report suspected phishing emails – provide relevant training, review internal processes that are in danger of exploitation, make reporting straightforward
- Protect your organisation from the effects of undetected phishing emails – set up two-factor authentication on your accounts, update your browsers, etc.
- Respond quickly to incidents – encourage users to report suspicious activity, and plan for different types of incidents
10. Provide Relevant Training
Make sure both you and your employees are trained to recognise suspicious activity and to know how to respond. Business owners and management should know what controls to put in place, but employees should also be trained on what to do if they come across or are a victim of a cyber attack so they can prevent a situation worsening.

Cyber Security, Internet, Email & Social Media, and Phishing Awareness training courses are essential tools in protecting your organisation from digital threats. Make sure you don’t miss out on our 10% off deal on these courses, available until the end of December. Simply enter the code ‘cyber10’ at checkout to save!
Read more Top 10 Tips blogs here.
To keep up to date with the latest health & safety news and advice, follow us on social media:
